Optus Hack: Data breaches are costly for both individuals and businesses. They can upend peoples’ lives, and put pressure on businesses to invest precious resources in securing and protecting customer data. The recent Optus hack is a prime example.
Not only did it result in many Aussies having to scramble to replace hacked IDs to safeguard against identity theft, Optus’ reputation took a mighty hit. It was among the largest data breaches in Australian history, exposing the personal information of almost 10 million customers, past and present.
Unfortunately, data breaches of this kind are becoming more common. But blockchain offers a technology that could potentially prevent the worst impacts of future Optus-style data breaches while also giving individuals control and ownership of their own data. his technology is blockchain-enabled decentralised identity.
If rolled out widely, in addition to the numerous benefits to individuals, decentralised identity could substantially relieve businesses of the burden of securing personal data, leading to significant cost savings and improved data security.
Data breaches cost business and individuals
Data breaches are expensive for businesses and those costs are rising. The IBM ‘Cost of a Data Breach Report 2022’ found that the average cost to businesses of a data breach globally had risen from US$3.86 in 2020 to US$4.35 million in 2022, an increase of 13 percent.
“83% of organizations studied have had more than one data breach.”
IBM Cost of a Data Breach Report 2022
The 2021 edition of IBM’s report showed the main way businesses are affected is lost business — customers don’t want to deal with companies that can’t protect their personal information. Lost business accounts for 38 percent of the total cost of data breaches, and in addition to losing customers, it includes costs associated with system downtime and the cost of acquiring new customers due to loss of reputation.
The costs to individuals from data breaches are harder to quantify financially, but can include the time and costs of having identity documents re-issued and monitoring their credit ratings to detect suspicious activity. In the worst case scenario, people’s stolen data can result in identity theft and fraud which can be financially and personally devastating.
The Optus hack shows we need a better system
The Optus hack illustrates just how vulnerable current models of identity and security are to hacks. Based on initial reports, it seems this hack wasn’t particularly sophisticated. Rather, it’s alleged to have been largely the result of human error.
A senior Optus insider speaking to the ABC claimed the data was accessed by the hacker through an unsecured application programming interface (API) end-point, which Optus had created for internal use to make it easier for its developers to implement two-factor-authentication.
Allegedly, the API end-point was inadvertently exposed to the internet at some point — resulting in all Optus customer records being publicly accessible on the internet. And of course, a hacker was ready to take advantage.
Why more centralisation is not the solution
The ease with which such large quantities of highly sensitive data — including driver licence, passport and Medicare card data — were accessed, points to the need for new ways of thinking about identity and security.
Since the Optus hack, the government has already suggested a new system that would involve a centralised identity database run on the MyGov system, which could be accessed by organisations like Optus to verify customers.
This kind of solution may relieve the burden on businesses somewhat, but it’s been met with scepticism by many, who claim it would further concentrate government control of individuals’ identities and create a very attractive future target for hackers – a so-called ‘honeypot’ for potential attackers.
The Blockchain-based identity alternative
Decentralised identity (DI) is a potentially revolutionary approach to identity which allows individuals to generate, control, and manage their personally identifiable information (PII), without needing to rely on centralised organisations.
In a DI model, an individual’s data is stored securely in their own self-sovereign identity (SSI) wallet app, rather than being scattered across potentially insecure databases all over the internet. The data stored in this wallet is cryptographically secured meaningno passwords are used. The data is also signed by relevant trusted authorities (such as government, work places etc.) to ensure its accuracy and to allow the data to be transmitted securely to other organisations or individuals as required.
By using a cryptographically secured, blockchain-based model, in which individual’s control their own identities, DI systems eliminate many of the attack vectors traditionally exploited by hackers — such as weak passwords and poor organisational data security practices — while also giving individual’s full control of their identities.
“By allowing the individuals true ownership of their digital identity, Decentralized Identity architectures abate the privacy concerns for individuals and security challenges for enterprises.”
Gartner Emerging Technologies: Critical Insights on Decentralized Identity, November 9, 2021
Optus Hack: Decentralisation
So what does a decentralised identity based system look like from an end user’s perspective? (Warning: jargon incoming!)
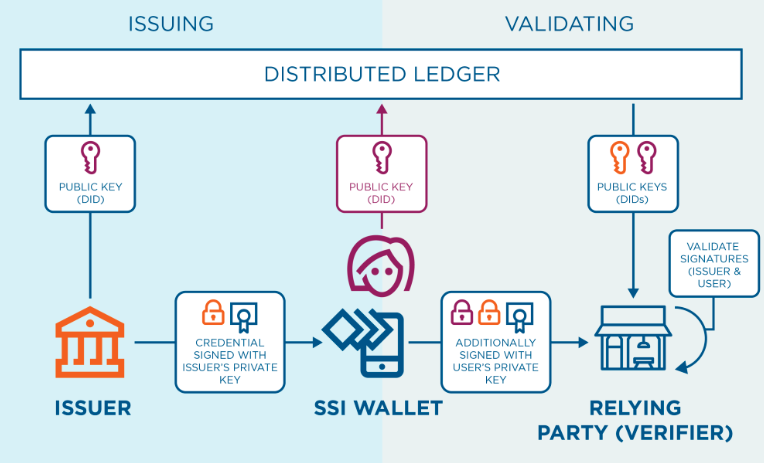
- An individual can use a specialised self-sovereign identity (SSI) wallet app to generate their own unique decentralised identifier (DID) based on their verified identity details, such as their name, age, and address.
- When a DID is generated, a public / private key cryptographic pair is also generated. The public key is published to a public distributed ledger (DLT), such as a blockchain.
- The individual can then use their DID, via their wallet, to request that an issuing organisation, such as a government department or university, issue them with a verifiable credential (VC) which can then be stored in their wallet. The issuing organisation cryptographically signs the VC to confirm its authenticity and accuracy.
- VCs could include digital versions of documents such as driver’s licences, passports or university qualifications, which can then be stored in the individual’s SSI wallet.
- Individuals can then grant access to organisations that require proof of their identity, such as when someone signs up for a telecommunications service like Optus. Once granted access, the organisation can look up an individual’s DID on a public distributed ledger and verify their identity and VCs stored in the user’s SSI wallet.
Crucially, this process doesn’t involve the verifying organisation storing the personal information – an individual’s information always remains under their own control.
An alternate history of the Optus hack in a world with decentralised identity
So, could a decentralised identity model have prevented the Optus hack?
Maybe not the hack itself, which was allegedly due to an unsecured API end-point. But it certainly would’ve minimised the damage caused.
Let’s take a look at the common case of a user being required to show their driver’s licence to open a mobile phone account on Optus. In a decentralised identity system, rather than requiring the user to upload a photo of their licence or enter the reference number on a form, Optus could have instead simply requested to securely verify the driver’s licence VC stored in the user’s SSI wallet app.
Optus would not need to store any of this information: the data would just need to be verified as true, to enable the customer to open their account. With no need for data to be stored on an Optus server to begin with, if DI was in place the customer’s personal data could not have been exposed in a hack of its systems.
The future needs better identity solutions
Decentralised identity is not some far-off crypto dream, like Dogecoin becoming the global currency. DI is already being integrated with software from some of the world’s largest companies right now, including Microsoft.
Microsoft Entra, which was released earlier this year and is now included with every Azure Active Directory subscription, includes a decentralised identity solution based on open standards developed by the Decentralised Identity Foundation.
Optus Hack: Victims
Other large players, including IBM and SecureKey, have also created DI solutions that are starting to see some significant adoption. Verified.Me from SecureKey has partnered with the Canadian Government to provide decentralised identity solutions that allows users to sign-in to many government services and large financial institutions.
As bad as the Optus hack was for its victims, data breaches will become even more consequential as our daily lives become increasingly entwined with new online technologies like the metaverse and SoulBound tokens (non-transferrable NFTs that represent an identity).
Decentralised identity offers a truly robust and secure solution to digital identity that could not exist without distributed ledger technology. It gives individuals ownership and control of their identities, reduces a reliance on centralised government-led models, and relieves businesses of the burden and costs of securing sensitive personal data.
Let’s hope more organisations start to see the potential of decentralised identity before another data breach on the scale of the Optus hack again endangers the privacy of millions of Aussies.





