In the wee hours of Friday morning, March 13, a decentralised finance (DeFi) protocol called Euler Finance suffered a major hack, where a hacker (or most likely a team of hackers) managed to exploit the protocol for nearly US$200 million.
The stolen assets were comprised of a mix of niche cryptocurrencies including the algorithmic stablecoin DAI, wrapped Bitcoin (wBTC), Lido Staked ETH (stETH), and the US Dollar-pegged stablecoin USDC. In addition to the theft of the massive sum of cryptocurrency, the price of Euler’s native token, EUL, plunged more than 45%.
On March 15, Euler Finance sent an on-chain message to the hackers demanding the return of 90% of the stolen funds, or face the full force of the law.
“Following up on our message from yesterday. If 90% of the funds are not returned within 24 hours, tomorrow we will launch a $1M reward for information that leads to your arrest and the return of all funds.”
Euler Finance
It’s also worth noting here that the Euler Finance exploit came as a major surprise to many in the crypto community, as Euler is one of the most security-focused and well-audited DeFi protocols in the industry. A number of major blockchain security firms, including Omnisica, ZK Labs, Certora, Halborn, Sherlock and Solidified all conducted contract audits on Euler Finance starting in early 2021.
How did the attackers do it?
According to a detailed breakdown from blockchain security firm SlowMist, the attacker used what’s known as a ‘flash loan’ to deposit a large sum of borrowed crypto and then exploited a bug in the protocol’s software to free themselves of the conditions applied to that loan and escape with the money.
Flash loans are a type of loan specific to crypto. They are executed by a smart contract and enable users to borrow funds quickly without needing to post any ‘collateral’ — a sum of money put down to secure a traditional loan.
Typically, flash loans are repaid in full within the same transaction, but this time, the hacker managed to leverage a US$20 million loan to borrow nearly ten times this amount and then exploited a bug to avoid repaying the loans at all.
Euler hack — who did it?
In the days following the attack, the identity of the hacker remained completely unknown.
However, a recent investigation undertaken by the blockchain intelligence firm Chainalysis shows that US$167,000 (100 ETH) worth of the stolen funds were moved to a wallet associated with the ominously-named North Korean hacking consortium known as the ‘Lazarus Group’.
Still, this isn’t cut and dry evidence that the attackers were part of the Lazarus Group, with Chainalysis noting that this could very well be a sophisticated hacker looking to cover their tracks.
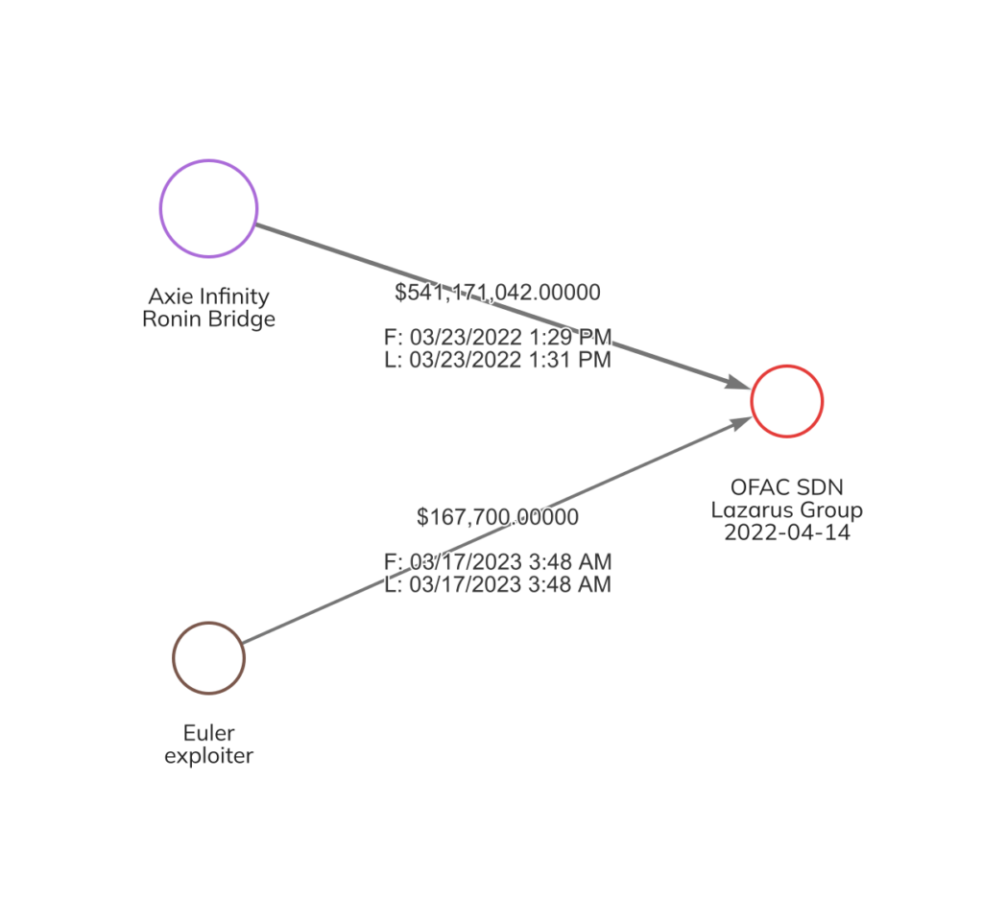
Lazarus Group have been responsible for some of the largest hacks in crypto history. In March last year, the hacking syndicate were identified as being responsible for the Ronin Bridge attack, which saw more than US$615 million stolen from the treasury of the popular play-to-earn game, Axie Infinity.
Following this initial transfer to the Lazarus-associated wallet, the hacker later moved 3,000 ETH (US$5.3 million) to a wallet associated with the Euler protocol itself. Additionally, another 1,000 ETH was transferred through a prohibited mixing service called Tornado Cash, a tool often used by hackers to obscure transaction history.
One of the most interesting parts of this entire saga came when a random Twitter user discovered that the hacker returned a sum of 100 ETH (US$165,00 at the time), to a victim that had pleaded with the hackers to return what was reportedly their “life savings.”
As of right now, no further transactions have been made. It remains unclear as to whether the hacker is simply poking fun at Euler by transferring the funds back to its deployer wallet, or if they are seriously weighing up the option of returning the funds.





